
In the digital era, cloud computing has become the backbone of operations for countless businesses worldwide. As organizations increasingly leverage cloud services to enhance efficiency and competitiveness, it’s imperative to recognize and address the top security challenges inherent in cloud computing. From data breaches to misconfigurations, understanding and proactively managing these cloud security risks are paramount to safeguarding sensitive information and ensuring business continuity.
As companies transition workloads to the cloud, they encounter many security concerns that demand attention. From the complexities of shared responsibility models to the ever-evolving threat landscape, navigating the intricacies of cloud network security requires a comprehensive strategy tailored to each organization’s unique needs. Through fostering a culture of awareness and implementing strong security measures, businesses can effectively mitigate risks and completely leverage the potential of cloud computing.
In this post, we’ll explore the top 10 security issues in cloud computing, offering insights into their implications and practical strategies for mitigation. From data privacy to access control, we’ll delve into critical considerations and cloud security best practices to empower organizations to navigate the cloud securely and unlock its transformative benefits. Join us as we embark on a journey to strengthen cloud network security and fortify the foundation of digital innovation.
Consult our Cloud Consulting Expert
Stats of Security Issues in Cloud Computing
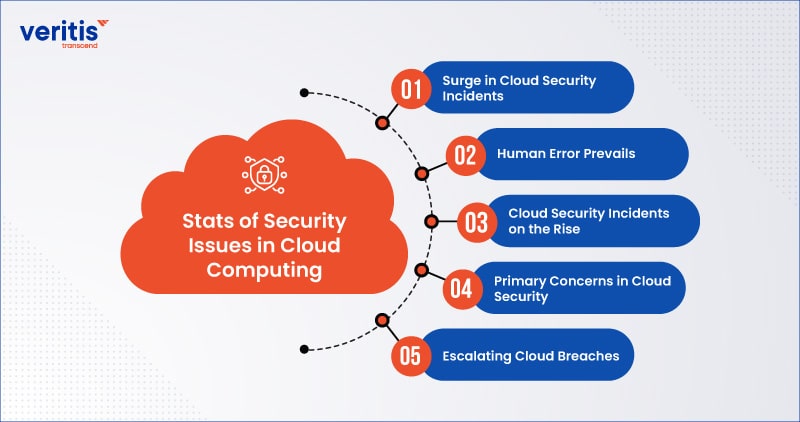
1) Surge in Cloud Security Incidents
Recent findings from Pingsafe indicate that 80% of organizations experienced a rise in cloud attacks throughout 2024, underscoring the escalating threat landscape within cloud environments.
2) Human Error Prevails
Secureframe’s report reveals that 82% of organizations attribute most cloud security solutions breaches to human error, emphasizing the pivotal role of comprehensive training and stringent security protocols for cloud users.
3) Cloud Security Incidents on the Rise
According to a recent survey by Snyk, 80% of firms experienced at least one cloud security incident in the past year, with public cloud breaches increasing by 10% to reach 27%. With 45% of breaches occurring in cloud environments, the prevalence of such incidents underscores the risks associated with cloud reliance.
4) Primary Concerns in Cloud Security
Statista reports that the leading concerns in cloud security solutions include data loss and leakage, cited by 69% of respondents, and data privacy and confidentiality, which worries 66% of users. Additionally, accidental exposure of credentials is a concern for 44% of respondents. These findings highlight the most pressing issues confronting cloud security solutions.
5) Escalating Cloud Breaches
Data analysis from GetAstra suggests a worrisome trend. A notable 45% of data breaches in 2024 targeted cloud-based systems. This stark statistic underscores organizations’ need to bolster cloud security frameworks to safeguard sensitive data effectively.
Useful link: What is Cloud Computing?
What is Cloud Computing?
Cloud computing revolutionizes how we manage, access, and store data by delivering services over the Internet instead of relying on traditional on-premises servers or local storage devices. This innovative model eliminates the need for intricate server management, often called “serverless technology.” A key benefit of cloud computing is that it enables users to focus on their applications and data rather than managing the underlying infrastructure.
With its versatility, cloud computing accommodates various data types, including images, audio files, videos, documents, and more. Organizations and individuals can enjoy scalable, cost-effective, and flexible solutions for their data requirements by leveraging the robust data security in cloud computing. This shift to the cloud not only streamlines operations but also offers unparalleled convenience and accessibility, thanks to the omnipresence of the internet.
In today’s interconnected world, cloud computing has become indispensable, empowering countless applications and services to operate reliably and efficiently. Whether enhancing collaboration, optimizing workflows, or facilitating innovation, cloud computing is the cornerstone of modern computing, driving progress and enabling seamless connectivity across the digital landscape.
What is the Need for Cloud Computing?
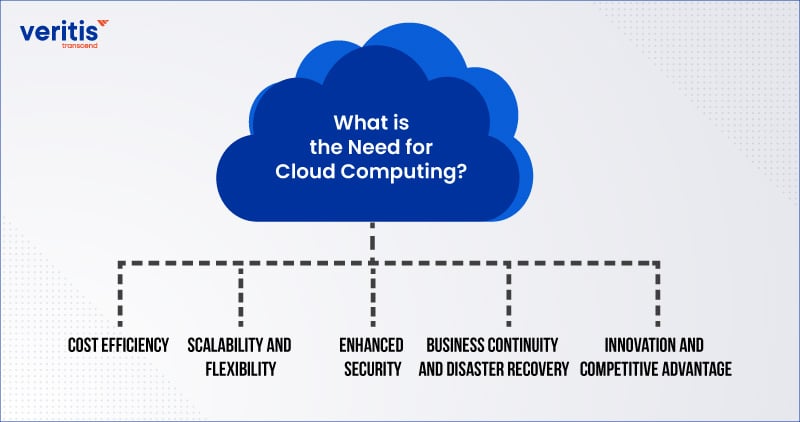
Cloud computing has revolutionized IT, offering businesses an attractive alternative to expensive on-premises setups. Through cloud migration, companies can utilize remote, secure data centers, cutting infrastructure costs and optimizing operations. This shift enhances efficiency, lowers costs, and empowers businesses with the flexibility and convenience needed to thrive in today’s dynamic digital environment.
1) Cost Efficiency
Cloud computing presents a cost-effective alternative to traditional on-premises setups, where companies must invest heavily in procuring, maintaining, and operating on-site infrastructure. By utilizing cloud services, organizations can substantially decrease infrastructure expenses, as they only pay for their resources, eliminating the necessity for upfront investments in hardware or infrastructure.
2) Scalability and Flexibility
Cloud computing offers unmatched scalability and flexibility, enabling businesses to adjust resources according to demand. This agility facilitates rapid adaptation to market shifts, handles sudden traffic increases, and manages fluctuating workloads without requiring costly hardware upgrades or additional infrastructure investments.
3) Enhanced Security
Cloud computing offers robust data security measures, such as authentication, access control, and encryption, to secure sensitive information against unauthorized access, breaches, and cyber threats. Leveraging advanced security protocols provided by cloud service providers helps organizations enhance their security posture and ensure compliance with industry regulations.
4) Business Continuity and Disaster Recovery
Cloud computing offers dependable disaster recovery and business continuity features, safeguarding vital data and applications from unforeseen events, including natural disasters, hardware failures, or cyberattacks. Through automated backup and recovery solutions provided by cloud providers, organizations can swiftly recover data and resume operations, reducing downtime and maintaining business continuity.
5) Innovation and Competitive Advantage
Cloud computing fuels innovation by empowering organizations to swiftly experiment, iterate, and launch new applications and services. Through harnessing advanced cloud technologies like AI, ML, and IoT, companies can glean insights, foster innovation, and keep a competitive edge in the digital era. With the agility and scalability offered by cloud computing, organizations can expedite the realization of ideas and capitalize on emerging prospects to attain enduring growth.
Useful link: 5 Cloud Computing Benefits to Automotive Industry
Cloud Security Challenges
The challenges lie in bridging the divide between theoretical knowledge and practical implementation. Understanding the importance of having a robust cloud security framework is one thing, but initiating the process and instigating a cultural shift can be daunting. The question arises: how does one begin? What are the concrete, day-to-day measures required to effect this change?
Embracing the cloud presents companies with four distinct cloud security challenges that are encountered universally:
1) Insufficient Cloud Security Expertise and Skillsets
2) Identity and Access Management
3) Shadow IT
4) Cloud Compliance
1) Insufficient Cloud Security Expertise and Skillsets
The transition to cloud computing requires a fundamental shift in security strategies and skill sets. The conventional security methods employed in on-premises data centers may not effectively tackle the distinct challenges presented by the cloud environment.
Cloud administrators must acquire fresh expertise tailored to the dynamic nature of cloud security solutions. While the cloud offers unparalleled organizational agility, it introduces new complexities and potential vulnerabilities. Many organizations struggle to keep pace with evolving cloud security requirements due to a lack of internal expertise. Insufficient grasp of the shared responsibility model, which delineates security duties between the cloud provider and the user, can heighten cloud security risks.
2) Identity and Access Management
IAM plays an essential role in cloud security, but its effective implementation presents a complex challenge with multiple dimensions. Creating and managing roles and permissions can seem like navigating a labyrinth for enterprises with sprawling employee bases. A robust IAM strategy encompasses three critical phases: role design, privileged access management, and seamless implementation.
The journey begins with meticulous role design, an exercise aimed at tailoring access permissions to match the diverse needs of cloud users. This entails crafting roles that transcend specific IAM platforms, focusing instead on delineating tasks every day across various cloud providers. By mapping out these roles comprehensively, organizations lay the groundwork for a streamlined IAM framework.
Next, a focused Privileged Access Management (PAM) strategy takes center stage, spotlighting roles wielding heightened privileges. These roles demand stringent access controls to safeguard against potential breaches. Tight control over privileged credentials and regular updates are imperative to mitigate cloud security risks effectively.
The final phase culminates in seamlessly implementing designed roles within the cloud provider’s IAM infrastructure. Organizations can navigate the implementation process with a meticulously crafted IAM blueprint with greater confidence and efficiency. By investing upfront in role design and PAM strategies, enterprises pave the way for a robust IAM framework that upholds security while facilitating seamless access to cloud resources.
3) Shadow IT
Shadow IT presents a significant security dilemma as it bypasses established IT protocols and oversight mechanisms, leaving organizations vulnerable to potential risks. This clandestine adoption of cloud services occurs as employees independently seek solutions to meet their operational needs, often without the knowledge or approval of IT departments. The inherent scalability of cloud resources exacerbates this challenge, as it becomes increasingly difficult to monitor and regulate the proliferation of shadow IT across the organization.
The advent of DevOps further complicates the landscape by prioritizing speed and agility in software development and deployment processes. While DevOps teams strive for rapid innovation and frictionless operations, their focus on efficiency may inadvertently overlook security considerations. This dynamic tension between speed and security underscores the need for a cohesive approach that bridges the gap between DevOps velocity and security requirements. Collaboration between IT, security, and DevOps teams is essential to devise unified solutions that provide security insights without impeding the agility of DevOps practices.
4) Cloud Compliance
Cloud compliance is essential for organizations handling sensitive data such as credit cards and healthcare records, necessitating adherence to PCI DSS and HIPAA regulations. Implementing strict access controls and user privileges is crucial, yet monitoring network access in the dynamic cloud environment poses challenges. Without robust measures, organizations risk non-compliance, exposing data to breaches and regulatory penalties. Maintaining compliance requires proactive solutions integrating stringent access controls, continuous monitoring, and agile responses to evolving standards.
Useful link: Cloud Computing in Healthcare: Looking for Security Advantage?
Top 10 Security Issues in Cloud Computing
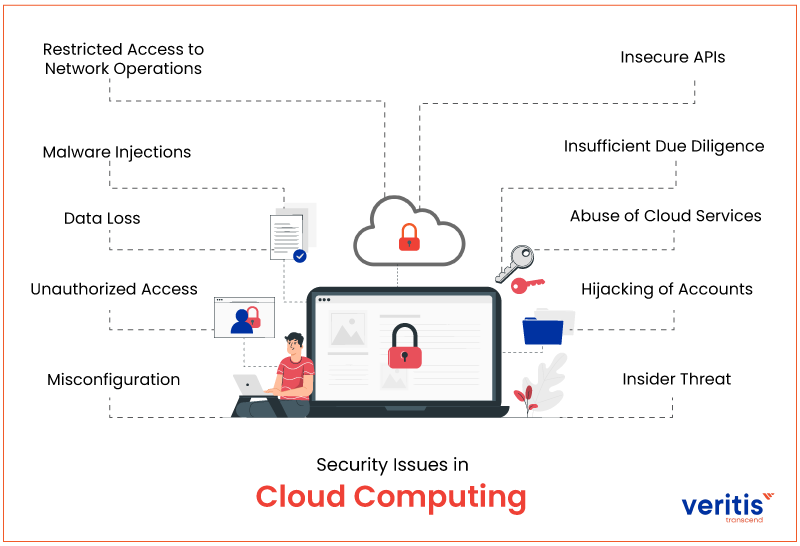
1) Misconfiguration
Misconfigurations in cloud security settings are a prevalent cause of data breaches, often resulting from inadequate security posture management practices. Cloud infrastructure’s user-friendly nature, designed for seamless data exchange, poses challenges in restricting data access to authorized entities. Consequently, enterprises relying on cloud service providers (CSPs) for security measures must ensure robust deployment and configuration of their cloud environments.
Lack of experience in cloud security and multi-cloud deployments further exacerbate vulnerabilities, emphasizing the critical need for comprehensive visibility and control over cloud infrastructure to mitigate risks effectively.
2) Unauthorized Access
Cloud-based installations, unlike on-premises infrastructure, are inherently accessible from the public Internet, extending beyond the confines of traditional network perimeters. While this accessibility fosters more significant user and customer engagement, it also heightens the risk of unauthorized access.
Attackers can exploit this accessibility to infiltrate a company’s cloud-based services, leveraging improperly configured security measures or compromised credentials. The covert nature of such attacks underscores the importance of robust security protocols and continuous monitoring to thwart unauthorized access attempts and safeguard sensitive data in the cloud environment.
3) Data Loss
Data loss, often called a data leak, poses a significant concern in cloud computing environments. With insiders such as employees and business partners granted access to sensitive data, the risk of unauthorized access by malicious actors increases. Enterprises leveraging cloud computing solutions must entrust some of their data security responsibilities to the Cloud Service Provider (CSP), potentially relinquishing control over critical data protection measures.
The reliance on external entities for data security in cloud computing introduces inherent risks, as breaches or attacks targeting the CSP can result in losing vital data and intellectual property. Organizations may face severe repercussions in such scenarios, including legal liabilities and reputational damage. Mitigating the risk of data loss in the cloud requires robust security protocols, comprehensive risk assessments, and proactive measures to ensure data integrity and confidentiality.
4) Malware Injections
Malware injections represent a significant threat to cloud computing security issues. Malicious scripts or code fragments masquerade as legitimate components within cloud services. These clandestine intrusions can compromise data integrity and operations, allowing attackers to eavesdrop, manipulate sensitive information, and exfiltrate data undetected.
The seamless integration of malware into cloud environments poses a grave security risk, as highlighted in the East Carolina University Report on Cloud Security Threats and Vulnerabilities. Addressing the menace of malware injections demands vigilant monitoring, robust security measures, and proactive detection and mitigation strategies to safeguard cloud infrastructure and protect against potential breaches.
5) Restricted Access to Network Operations
Transitioning from on-premises data storage to cloud-based infrastructure brings a trade-off between benefits like cost savings and scalability and the potential drawback of limited visibility into network operations. Enterprises entrust varying degrees of control to Cloud Service Providers (CSPs) in exchange for these advantages, raising concerns about data security and access control.
The extent of CSP control and enterprises’ data security obligations vary based on the service model adopted. However, the persistent lack of insight into cloud environments poses an ongoing security threat for organizations relying on them for critical data management. This underscores the significance of security measures and continuous monitoring to mitigate risks effectively.
Useful link: What You Should Know About Containers Threats in Cloud Computing
6) Insecure APIs
While application programming interfaces (APIs) empower customers to customize their cloud security tools, they also introduce inherent cloud security risks. APIs are pivotal in authentication, access control, and encryption, enabling businesses to tailor their cloud infrastructure services to meet specific requirements. However, as API infrastructure expands to enhance service offerings, so do the associated cloud security threats.
APIs afford flexibility and functionality, enabling developers to create custom programs and seamlessly integrate them with mission-critical software. Yet, the communication between applications that APIs facilitate also exposes organizations to potential cloud security vulnerabilities. While API-driven customization offers numerous benefits, businesses must prioritize vigilance and implement robust security measures to mitigate the risks associated with insecure APIs effectively.
7) Insufficient Due Diligence
Amidst the technical complexities of cloud security, the human element often emerges as a critical factor in ensuring robust protection. Insufficient due diligence, characterized by a lack of clear strategic objectives, resource allocation, and adherence to established cloud security frameworks, can expose businesses to significant cloud security risks.
Rushing into multi-cloud deployment migrations without thorough planning and assessment of service capabilities may jeopardize compliance with regulatory standards such as FERPA, PCI, PCI-DSS, and PII. For organizations entrusted with sensitive client financial data or subject to stringent regulatory requirements, diligent due diligence is paramount to mitigate potential security vulnerabilities and uphold data integrity and compliance.
8) Abuse of Cloud Services
The widespread adoption of cloud-based services has enabled businesses of various scales to store large volumes of data securely. However, the cloud’s unprecedented storage capacity also allows for abuse, allowing malicious software and unauthorized digital goods to be hosted and distributed by authorized users and hackers.
This misuse compromises the integrity of the cloud service provider and poses significant cloud security risks for its clients. Privileged users may inadvertently or deliberately violate service provider terms, exacerbating cloud computing security issues. Diligent monitoring and strict enforcement of usage policies are essential to reduce the risks linked with the misuse of cloud services and to maintain data integrity and security.
9) Hijacking of Accounts
As enterprises increasingly adopt cloud security tools, the threat of account hijacking has emerged as a significant concern. Attackers can exploit compromised login credentials to remotely access sensitive data stored in the cloud, manipulate information, and even falsify data. While traditional methods such as phishing, keylogging, and buffer overflow attacks persist, a new threat known as the Man-in-the-Cloud Attack has emerged.
This sophisticated attack involves stealing tokens cloud service providers utilize to validate individual devices. This enables unauthorized access to cloud accounts and data without requiring repeated logins. Mitigating this risk requires robust security measures, including multi-factor authentication and continuous monitoring, to thwart unauthorized access attempts and safeguard sensitive information stored in the cloud.
10) Insider Threat
Despite seeming improbable, insider cloud security threats pose a significant risk to organizations utilizing cloud-based services. Employees with authorized access to company resources may intentionally or inadvertently misuse sensitive data, including client accounts and financial information.
Furthermore, insider cloud security threats are not limited to malicious intent; inadvertent actions or negligence can also result in security breaches. Establishing strong access controls, conducting employee training initiatives, and maintaining ongoing monitoring are crucial to mitigate insider threats and protect sensitive data stored in the cloud.
Conclusion
While the cloud offers unparalleled opportunities for storage, accessibility, and productivity, it also brings forth a host of security challenges. By understanding and addressing these top 10 cloud computing security concerns, businesses can formulate robust multi-cloud deployment strategies to protect their assets effectively.
Veritis, a distinguished recipient of prestigious accolades such as the Stevie and Globee Business Awards, stands ready to assist. With our top-notch cloud consulting services, we provide cutting-edge security services tailored to your unique needs, whether you’re transitioning to the cloud or already established there. Partner with Veritis to ensure the security and resilience of your cloud-based systems, empowering your business to thrive in dynamic market environments.
Explore Cloud Services Got Questions? Schedule A Call
Additional Resources:
- 6 Ways Why Cloud Based Solutions Benefit Small and Medium Sized Enterprises (SMEs)
- Cloud Adoption Strategy: Which Approach Would be Most Effective for Your Company?
- What is Cloud Migration? Strategy, Process, and Tools
- Global Cloud Market to Reach Nearly USD 800 Billion by 2028: Survey
- Cloud Security Automation: Best Practices, Strategy, and Benefits
- 9 Keys to Selecting a Right Cloud Managed Services Provider (MSP)
- Cloud Infrastructure Automation: The Imperative for Cloud Success!
- Cloud Computing: Trends, Challenges and Benefits